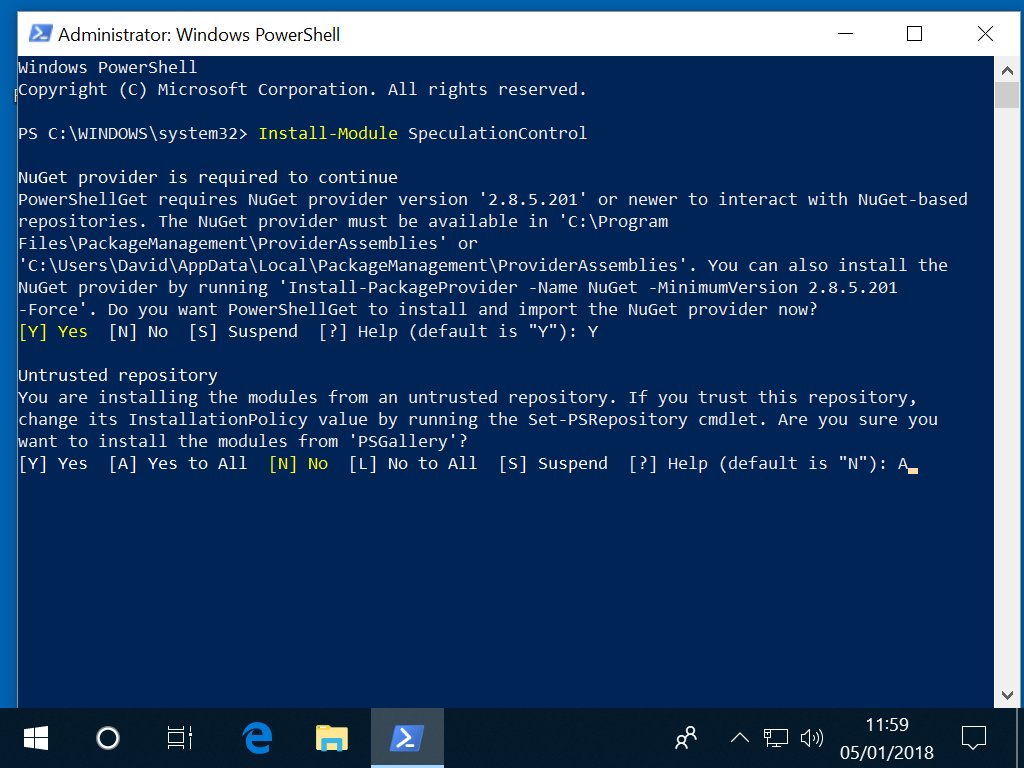
This needs Nuget and to trust the PSGallery
The basic issue is that speculative execution affects the cpu state even for intstructions we do not have permission to execute which allows indirect inference of values in kernel memory i.e. reading kernel memory
The list of issues is:
| Codename | Variant | CVE | Type |
|---|---|---|---|
| Spectre | Variant 1 | CVE-2017-5753 | bounds check bypass |
| Spectre | Variant 2 | CVE-2017-5715 | branch target injection |
| Meltdown | Variant 3 | CVE-2017-5754 | rogue data cache load |
Explainations are at:
| Owner | Reference |
|---|---|
| Google Project Zero | Project Zero |
| Klaus Aschenbrenner | Understanding the Meltdown exploit – in my own simple words |
Proof of concept Windows Exploit code is at code for the cache-attack
As per Meltdown, Spectre bug patch slowdown gets real – and what you can do about itvarious groups have reported slowdowns between 1 and 45 percent
Azure VMS in Western Europe were down following patching Azure VMs borked following Meltdown patch, er, meltdown
Advice from Microsoft for Azure VMS is at Securing Azure customers from CPU vulnerability
There is also a KB article at Microsoft cloud protections against speculative execution side-channel vulnerabilities
See also Securing Azure customers from CPU vulnerability
As per Meltdown, Spectre: The password theft bugs at the heart of Intel CPUs
"Amazon has updated its AWS Linux guest kernels to protect customers against Meltdown."Processor Speculative Execution Research Disclosure
UPDATE: Jan 23 as per Meltdown and Spectre, explained "At Lyft, we saw an approximately 20% slowdown on certain system call heavy workloads on AWS C4 instances when the mitigations were rolled out."
"at Lyft we are aggressively moving some workloads to AWS C5 instances due to the fact that IBRS appears to run substantially faster on Skylake processors and the new Nitro hypervisor delivers interrupts directly to guests using SR-IOV and APICv, removing many virtual machine exits for IO heavy workloads)"
Amazon VMS reported slowdowns after patching Amazon: Intel Meltdown patch will slow down your AWS EC2 server
Google has advice at What Google Cloud, G Suite and Chrome customers need to know about the industry-wide CPU vulnerability
UPDATE: 15th Jan: As per Storage slingers say: Don't sweat Spectre, Meltdown SANitation Google has said Protecting our Google Cloud customers from new vulnerabilities without impacting performance "With Retpoline, we didn't need to disable speculative execution or other hardware features. Instead, this solution modifies programs to ensure that execution cannot be influenced by an attacker. With Retpoline, we could protect our infrastructure at compile-time, with no source-code modifications.
"Furthermore, testing this feature, particularly when combined with optimizations such as software branch prediction hints, demonstrated that this protection came with almost no performance loss."
"We believe that Retpoline-based protection is the best-performing solution for Variant 2 on current hardware. Retpoline fully protects against Variant 2 without impacting customer performance on all of our platforms. In sharing our research publicly, we hope that this can be universally deployed to improve the cloud experience industry-wide."
See CPU Vulnerabilities: Meltdown & Spectre
See Open Telekom Cloud Security Advisory about Processor Speculation Leaks (Meltdown/Spectre)
VMWare has a security announcement at [Security-announce] NEW VMSA VMSA-2018-0002 VMware ESXi, Workstation and Fusion updates address side-channel analysis due to speculative execution
There is also an entry on the VMware Security & Compliance Blog at VMSA-2018-0002
There are also updates for ESXi, Workstation and Fusion at VMSA-2018-0002 VMware ESXi, Workstation and Fusion updates address side-channel analysis due to speculative execution.
UPDATE Jan 10: Even though this lists VMware Workstation 14.x as unaffected VMware Workstation 14.1.1 Pro Release Notes mentions "This update of VMware Workstation Pro exposes hardware support for branch target injection mitigation to VMware guests. This hardware is used by some guest operating systems to mitigate CVE-2018-5715 (also called by the name "Spectre")."
"For Guest Operating Systems to be able to use hardware support for branch target injection mitigation, the following steps must be taken:
"
UPDATE Jan 11: Even though this lists VMware Fusion 10.x as unaffected VMware Fusion 10.1.1 Release Notes mentions "This update of VMware Fusion exposes hardware support for branch target injection mitigation to VMware guests. This hardware is used by some guest operating systems to mitigate CVE-2018-5715 (also called by the name "Spectre").."
"For Guest Operating Systems to be able to use hardware support for branch target injection mitigation, the following steps must be taken:
UPDATE Jan 12: VMWare has a new security announcement at VMSA-2018-0004 VMware vSphere, Workstation and Fusion updates add Hypervisor-Assisted Guest Remediation for speculative execution issue
Also there is a knowledge base article at VMware Response to Speculative Execution security issues, CVE-2017-5753, CVE-2017-5715, CVE-2017-5754 (aka Spectre and Meltdown) (52245)
VMware is providing several versions of the required microcode from INTEL and AMD through ESXi patches listed in the table. See Hypervisor-Assisted Guest Mitigation for branch target injection (52085) for more details.
The new versions of vCenter Server set restrictions on ESXi hosts joining an Enhanced vMotion Cluster See Hypervisor-Assisted Guest Mitigation for branch target injection (52085) for more details.
From VMware Knowledge Base article 52085:
To enable hardware support for branch target mitigation in vSphere, apply these steps, in the order shown:
To enable hardware support for branch target mitigation in Workstation/Fusion, the following steps should be followed:
| Product |
|---|
| Workstation 14.1.1 |
| Workstation 12.5.9 |
| Fusion 10.1.1 |
| Fusion 8.5.10 |
For each virtual machine, enable Hypervisor-Assisted Guest mitigation via the following steps:
Xen have an advisory at Advisory XSA-254
See QEMU and the Spectre and Meltdown attacks
The Microsoft Security Advisory covering Windows,SQL Server,Internet Explorer and Microsoft Edge is at: ADV180002 | Guidance to mitigate speculative execution side-channel vulnerabilities Security Advisory
UPDATE Jan 10: As per Endpoint Protection system tray icon reports multiple errors after applying Windows security updates from 1/3/2018 Symantec "recommends that the Microsoft Windows Security Updates released on January 3rd, 2018 updates not be applied to systems until a hotfix is available for the affected versions.".
"After applying Microsoft Windows security updates released on January 3rd, 2018, the Symantec Endpoint Protection (SEP) system tray icon reports there are multiple problems. No errors are reported if the SEP client UI is opened."
"At this time, this issue has no functional impact on the protection technology of the SEP client."
As per Twitter from Adam Licata Principal Product Manager for Endpoint Security at Symantec "The UI fix is undergoing QA testing this week and will be released soon"
UPDATE: 10 Jan - Kevin Beaumont has a spreadsheet with a list of anti-virus products and patch compatability at Twitter
Microsoft has issued patches for:
| Operating System | Reference |
|---|---|
| Windows 10 | January 3, 2018—KB4056892 (OS Build 16299.192)UPDATE Jan 10th, pulled for some AMD devices, see below |
| Windows Server 2008,2008R2,2012,2012 R2,2016,1709 Server Core | https://support.microsoft.com/en-us/help/4072698/windows-server-guidance-to-protect-against-the-speculative-execution |
The Windows 10 fix is currently pulled for some AMD devices
UPDATE Jan 9th, this can brick AMD Althon 64 Pc's It gets worse: Microsoft’s Spectre-fixer bricks some AMD PCs
UPDATE Jan 10th Windows operating system security update block for some AMD based devices "Microsoft is working with AMD to resolve this issue and resume Windows OS security updates to the affected AMD devices via Windows Update and WSUS as soon as possible."
If the machine is in an unbootable state see the following resources to help:
| Operating System | Reference |
|---|---|
| Windows 10 | Troubleshoot blue screen errors |
| Windows 8.1 | Resolving Blue Screen errors in Windows |
| Windows 7 | Resolving stop (blue screen) errors in Windows 7 |
Certain registry keys need to be set to activate the fixes
These are in links from the table above however for reference they are
On Windows 10 there have been blue screens due to certain anti-virus software, once confirmed the anti-virus sofrware is fixed the following registry key is needed
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\QualityCompat" /v cadca5fe-87d3-4b96-b7fb-a231484277cc /t REG_DWORD /d 0
On Windows server due to performance issues, to activate the fixes 3 registry keys need to be set
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0 /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization" /v MinVmVersionForCpuBasedMitigations /t REG_SZ /d "1.0" /f
Then if this is a Hyper-V host: fully shutdown all Virtual Machines.
Restart the server for changes to take effect.
To then disable the fix only 2 registry changes are needed:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 3 /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Restart the server for changes to take effect.
For Hyper-V hosts, live migration between patched and unpatched hosts may fail: see Protecting guest virtual machines from CVE-2017-5715 (branch target injection)
Also as per More stuff broken amid Microsoft's efforts to fix Meltdown/Spectre vulns "Unless the antivirus compatibility registry key is set, Windows Update will not delivery January's or any future security updates."
The registry key and antivirus vendors
As per CPU bug patch saga: Antivirus tools caught with their hands in the Windows cookie jar
Sentinel One explained in a blog post Meltdown/Spectre – A tale of two vendors that
"This is because our customers may have other software products that use unsupported/undocumented APIs that are incompatible with Microsoft’s latest patches. In such a case, our customers may experience stop errors/system instabilities caused by other products that are not compatible with Microsoft fixes."
"This is why we’re giving our customers the choice of whether to set the registry key, instead of forcing a solution on them that presents the risk of a real meltdown. While some vendors in the market are taking the approach of checking for incompatible software, we do not believe that this approach can be done in a comprehensive manner."
"Because of this, we are strongly recommending that our customers test the patch with our agent and their full stack of software applications before setting the registry key."
Checking the fix has been applied
The simplest test for the fix having been applied is
This needs Nuget and to trust the PSGallery

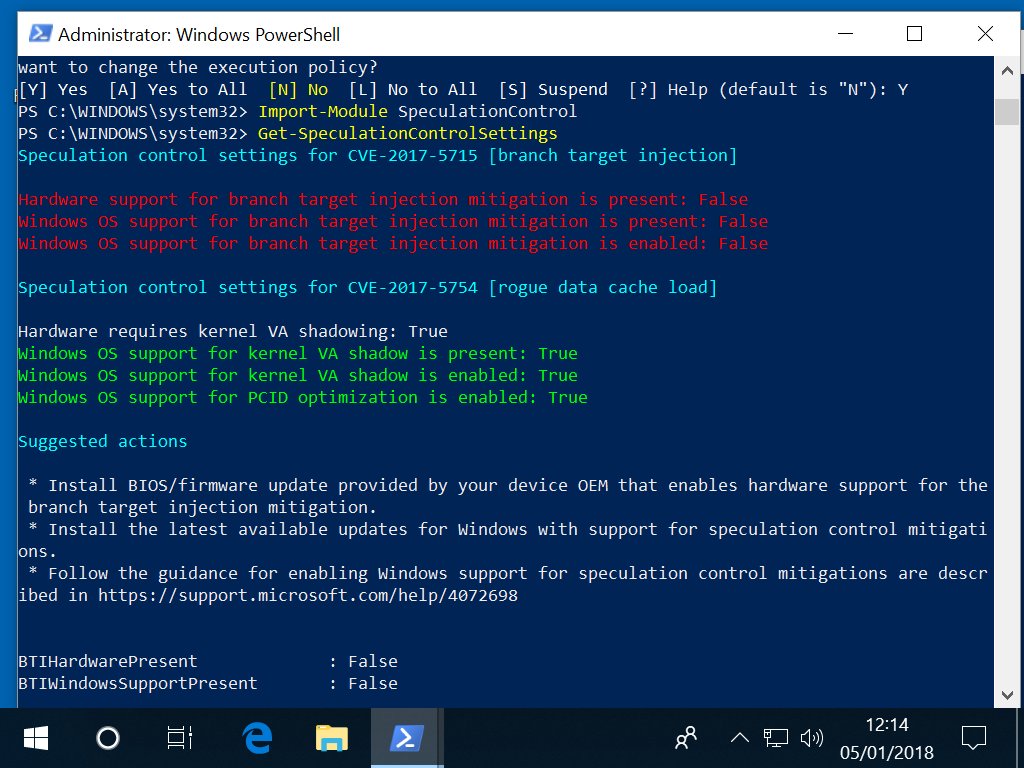
NOTE: "In addition to installing the January security update, a processor microcode update is required. This should be available through your OEM."
NOTE Also that as per More stuff broken amid Microsoft's efforts to fix Meltdown/Spectre vulns these updates break both the PulseSecure VPN client and Sandboxie, the sandbox-based isolation program developed by Sophos.
PulseSecure has a workaround for Windows 10 and Windows 8.1 but not Windows 7 at KB43600 - After installing January 3, 2018 Microsoft Patches, Pulse client connections fail when Host Checker is applied
Sandboxie has an updated BETA client available at 5.23 Beta Available (latest version 5.23.3)
As per Intel, Microsoft confess: Meltdown, Spectre may slow your servers Microsoft have confirmed slowdown after applying the patches"
Terry Myerson, president of Microsoft's Windows and device group confirmed in Understanding the performance impact of Spectre and Meltdown mitigations on Windows Systems that some slowdown is expected:
| Operating System | Processor | Impact |
|---|---|---|
| Windows 10 | Newer silicon (2016-era PCs with Skylake, Kabylake or newer CPU) | Benchmarks show single-digit slowdowns, but we don’t expect most users to notice a change because these percentages are reflected in milliseconds. |
| Windows 10 | Older silicon (2015-era PCs with Haswell or older CPU) | Some benchmarks show more significant slowdowns, and we expect that some users will notice a decrease in system performance. |
| Windows 8 and Windows 7 | older silicon (2015-era PCs with Haswell or older CPU) | we expect most users to notice a decrease in system performance. |
| Windows Server | any silicon (processor) | Any IO-intensive application, shows a more significant performance impact when you enable the mitigations to isolate untrusted code within a Windows Server instance. This is why you want to be careful to evaluate the risk of untrusted code for each Windows Server instance, and balance the security versus performance tradeoff for your environment. |
"For context, on newer CPUs such as on Skylake and beyond, Intel has refined the instructions used to disable branch speculation to be more specific to indirect branches, reducing the overall performance penalty of the Spectre mitigation."
"Older versions of Windows have a larger performance impact because Windows 7 and Windows 8 have more user-kernel transitions because of legacy design decisions, such as all font rendering taking place in the kernel."
As per Meltdown and Spectre Linux Kernel Status
Meltdown - x86 "If you rely on any other kernel tree other than 4.4, 4.9, or 4.14 right now, and you do not have a distribution supporting you, you are out of luck."
Meltdown - ARM "Right now the ARM64 set of patches for the Meltdown issue are not merged into Linus’s tree. They are staged and ready to be merged into 4.16-rc1 once 4.15 is released in a few weeks."
Due to them not being in a released kernel, if you rely on ARM64 for your systems (i.e. Android), I point you at the Android Common Kernel tree All of the ARM64 fixes have been merged into the 3.18, 4.4, and 4.9 branches as of this point in time."
"For the 4.4 and 4.9 LTS kernels, odds are these patches will never get merged into them, due to the large number of prerequisite patches required. All of those prerequisite patches have been long merged and tested in the android-common kernels, so I think it is a better idea to just rely on those kernel branches instead of the LTS release for ARM systems at this point in time."
Spectre "For upstream, well, the status is there is no fixes merged into any upstream tree for these types of issues yet."
Additional information is at Addressing Meltdown and Spectre in the kernel
Patches include
Retpoline: Binary mitigation for branch-target-injection (aka "Spectre") (repoline)
IBRS patch series (indirect branch restricted speculation)
API for inhibiting speculative arbitrary read primitives(disable arbitrary reads)
As per Meltdown/Spectre week three: World still knee-deep in something nasty to check if you are protected:
grep . /sys/devices/system/cpu/vulnerabilities/*
UPDATE : 15 Jan As per Meltdown/Spectre mitigation for 4.15 and beyond
Variant 1: in the latest patch set from Dan Williams PATCH v3 0/9] core, x86: prevent bounds-check bypass via speculative execution the proposed nospec_array_ptr() macro has been renamed to just array_ptr(). Also "The initial implementation used the Intel-blessed mechanism of inserting an lfence instruction as a barrier to prevent speculation past the bounds check. But barriers are relatively expensive" the new mechanism is to "ensure that any speculation that does occur remains within the bounds of the array being accessed"!
Variant 2: retpoline was merged into the mainline at the 4.15-rc8 release however as per below Skylake CPUS need a fix for the return stack buffer (RSB), an RSB underflow will cause a fallback to the branch prediction buffer
"It may also be possible, on some other processors, for user space to populate the RSB with hostile values, once again enabling the wrong kind of speculation. The answer in either case is the same: stuff the RSB full of well-known values in places (like context switches) where things could go wrong. The RSB-stuffing patches have been circulating for a while; they have not yet been merged but that should happen in the near future."
The gcc compiler option was changed to -mindirect-branch=thunk-extern requiring further kernel patches [PATCH] x86/retpoline: Switch thunk names to match final GCC patches
"The remaining concern on Skylake processors would appear to be system-management interrupts (SMIs), which can cause unprotected code to be run in kernel context." David Woodhouse at Re: Improve retpoline for Skylake stated the plan is to use microcode IBRS for Skylake with further work to make retpoline completely safe on Skylake.
Variant 3: Kernel Page Table Isolation (KPTI) causes a slowdown so Willy Tarreau has been working on a patch set [RFC PATCH v3 0/8] Per process PTI activation to exclude performance critical processes from KPTI.
Willy Tarreau patch set added ptrace operations ARCH_DISABLE_PTI_NOW to disable KPTI for the current process and ARCH_DISABLE_PTI_NEXT which sets a flag to disable KPTI after an execve(), Linus only wants ARCH_DISABLE_PTI_NEXT
There is an assocaited capability CAP_SYS_RAWIO and sysctl knob /proc/sys/vm/pti_adjust
As per Re: [RFC PATCH v2 6/6] x86/entry/pti: don't switch PGD on when pti_disable is set Andy Lutomirski proposes a new capabaility CAP_DISABLE_PTI for the feature
UPDATE : 23 Jan Also see the entry for Intel CPUS for an issue with Intel Skylake CPUS and issues on a 'ret' in some circumstances (such as 16+ CALLs in a deep chain) where Linux Kernel Mailing List discussions are ongoing
Redhat has patches under "Resolve" at Red Hat slams into reverse on CPU fix for Spectre design blunder
Discussion regarding the performance impact of patches is at Speculative Execution Exploit Performance Impacts - Describing the performance impacts to security patches for CVE-2017-5754 CVE-2017-5753 and CVE-2017-5715
UPDATE: Jan 18: As per Kernel Side-Channel Attacks - CVE-2017-5754 CVE-2017-5753 CVE-2017-5715 "Latest microcode_ctl package will not contain mitigation for CVE-2017-5715 (Spectre, Variant 2)"
Here's a key part of the letter to customers, seen by El Reg: "Historically, for certain systems, Red Hat has provided updated microprocessor firmware, developed by our microprocessor partners, as a customer convenience. Further testing has uncovered problems with the microcode provided along with the “Spectre” CVE-2017-5715 mitigation that could lead to system instabilities. As a result, Red Hat is providing a microcode update that reverts to the last known and tested microcode version dated before 03 January 2018 and does not address “Spectre” CVE-2017-5715."
Here's the next part of the customer note: "In order to mitigate “Spectre” CVE-2017-5715 fully, Red Hat strongly recommends that customers contact their hardware provider for the latest microprocessor firmware updates."
SuSE Linux patches are at Security Vulnerability: "Meltdown" and "Spectre" side channel attacks against modern CPUs.
The SuSE Linux response to the issues is at SUSE Addresses Meltdown and Spectre Vulnerabilities
OpenSUSE status is at Current Status: openSUSE and “Spectre” & “Meltdown” vulnerabilities
Ubuntu has a response to the issues at Information Leak via speculative execution side channel attacks (CVE-2017-5715, CVE-2017-5753, CVE-2017-5754 aka Spectre and Meltdown)
Patches will appear under Ubuntu security notices
Currently we only see USN-3516-1: Firefox vulnerabilities
UPDATE: 15th Jan as per Meltdown Update Kernel doesnt boot
"Using a Dell Poweredge T20 and Ubuntu 16.04 with the 4.4 Kernel."
"Just got the Meltdown update to kernel linux-image-4.4.0-108-generic but this doesnt boot at all. It just hangs after grub. There is no logs from syslog or such. SysReq Keys dont work neither."
"The last kernel linux-image-4.4.0-104-generic still boots fine."
"4.4.0-109, which is now available as security update from regular Ubuntu repositories, works on all three servers of mine which panic'ed with 4.4.0-108. Thank you Ubuntu kernel team!"
"For those of you having the same problem with me and Carter Braxton (low resolution in 4.4.0-109 kernel). You need to PURGE all 4.4.0-108 kernel image and the remaining HEADERS. Use command: sudo apt autoremove"
Apple have security update information at About the security content of macOS High Sierra 10.13.2, Security Update 2017-002 Sierra, and Security Update 2017-005 El Capitan
As per How to protect your PC from the major Meltdown and Spectre CPU flaws "Chromebooks should have already updated to Chrome OS 63 in December. It contains mitigations against the CPU flaws."
As per How to fix Meltdown and Spectre security flaws on Chromebooks
Check Chrome OS devices and kernel versions and "check that it says ‘yes’ in the last column".
UPDATE 10th Jan: Potential Impact on Processors in the POWER family
has been updated - "AIX and IBM i operating system patches will be available February 12. Information will be available via PSIRT."Also "The firmware patch provides partial remediation to these vulnerabilities and is a pre-requisite for the OS patch to be effective"
As per Android Security Bulletin—January 2018 "Security patch levels of 2018-01-05 or later address all of these issues"
There is a seperate bulletin for Pixel/Nexus devices at Pixel?/?Nexus Security Bulletins
As per Intel’s Meltdown fix freaked out some Broadwells, Haswells
"Oracle has patched its Linux, but has told us it has “No comment/statement on this as of now” in response to our query about its x86 systems, x86 cloud, Linux and Solaris on x86. The no comment regarding Linux is odd as fixes for Oracle Linux landed...on January 9th.
The Oracle Linux patches are at ELSA-2018-4006 - Unbreakable Enterprise kernel security update
UPDATE: 15th Jan Also see the entry for Oracle
See CVE-2017-5754
See Protect your Fedora system against Meltdown
See Response to Meltdown and Spectre
See Meltdown, aka "Dear Intel, you suck"
See Project:Security/Vulnerabilities/Meltdown and Spectre
See Container Linux patched to address Meltdown vulnerability
As per Meltdown/Spectre mitigation for 4.15 and beyond on Jan 15 Shawn Webb said ". In HardenedBSD, we've already switched amd64 to use ld.lld as the default linker. We're testing a full OS (world + kernel + packages) with retpoline right now. We'll likely debut retpoline in HardenedBSD 12-CURRENT/amd64 late this week or early next."
See HardenedBSD
As per Guide to protect SQL Server against speculative execution side-channel vulnerabilities
This mentions untrusted SQL Server extensibility mechanisms
NOTE: These are only for Windows! "The Microsoft Download Center will be updated with the remaining SQL Server versions as they become available in coming days/weeks, including SQL Server for Linux."
For SQL Server 2017 on Windows, CU3 may already been installed as part of Windows OS patchs: see Cumulative Update 3 for SQL Server 2017
UPDATE: 19 Jan - As per the first link above SQL Server on Linux patches are available
The fixes available are:
As per Actions required to mitigate Speculative Side-Channel Attack techniques"Chrome allows users to enable an optional feature called Site Isolation which mitigates exploitation of these vulnerabilities."
"Chrome's JavaScript engine, V8, will include mitigations starting with Chrome 64, which will be released on or around January 23rd 2018."
"In line with other browsers, Chrome will disable SharedArrayBuffer starting on Jan 5th, and modify the behavior of other APIs such as performance.now, to help reduce the efficacy of speculative side-channel attacks. This is intended as a temporary measure until other mitigations are in place."
As per comments in COMMENTS "Chrome 63 added a test feature one needs to turn on called Strict Site Isolation" instructions available at Increase security with site isolation
Firefox has fixes available in all release channels starting with 57 at Mitigations landing for new class of timing attack
Mozzila has an advisory at Speculative execution side-channel attack ("Spectre")
"Since this new class of attacks involves measuring precise time intervals, as a partial, short-term, mitigation we are disabling or reducing the precision of several time sources in Firefox. The precision of performance.now() has been reduced from 5µs to 20µs, and the SharedArrayBuffer feature has been disabled because it can be used to construct a high-resolution timer."
"Db2 will be impacted by any performance degradation caused by patches to other system components used by Db2. An assessment of the degree of impact on Db2 performance will be conducted. We will provide further information on this aspect as it becomes available."
"SharedArrayBuffer is already disabled in Firefox 52 ESR."
Microsoft browsers fixes are included in the Windows 10 and Window server OS patches above
As per Twitter from Paul Bird Senior Technical Staff Member IBM Toronto Lab, Lead Architect for DB2 for LUW server in areas of workload management, security, monitoring, and general SQL processing - "From a Db2 perspective, we don't see any Db2 patches needed at this time".
He recommends applying OS and firmware patches potentially via IBM BigFix as per IBM Insights and Recommendations on the CPU Vulnerability
UDPATE: Jan 14 Central Processor Unit (CPU) Architectural Design Flaws - additional guidance for Db2 customers
"At this time, we are not aware of any specific security exposures within Db2 itself on this issue."
Microsoft has advice on anti-virus program at Important: Windows security updates released January 3, 2018, and antivirus software
Also see 1.1.4.1 Microsoft Windows section "The registry key and antivirus vendors"
For Symantec enterprise software and hardware products see Meltdown and Spectre: Are Symantec Products Affected?
For Symantec Norton products see Meltdown and Spectre vulnerabilities affect billions of devices
See Introduce __builtin_load_no_speculate although this still needs review
See Introduce llvm.nospeculateload intrinsic although this still needs review
As per Another day, another Spectre fix slowdown: What to expect if you heart ZFS:
Systems engineer Jon Kensy blogged about his tests at Intel Microcode for Spectre/CVE-2017-5715 – Real performance loss in ZFS:
"The hit was 7-8 per cent for read IOPS and throughput, a negligible gain for write throughput and slight hit for write IOPS."
It was not a heavily stressed system. He writes: "For production environments where clients demand the best performance possible, a 7.6-8 per cent impact is pretty rough especially since the current tenor of this whole ordeal is one of being cheated out of performance."
Arman Khalatyan reports "I can confirm like Marek: maximum downgrade is about 40% by rsync with small files, lfs find on large folders 45% performance penalty:( We found terrible performance on the test system with zfs+compression+lustre. Good news: the compute node flops are about 1% or even none. So only IO intensive applications are impacted."
See [PATCH 0/3] Add __builtin_load_no_speculate
As per Meltdown/Spectre mitigation for 4.15 and beyond the compiler option was renamed to -mindirect-branch=thunk-extern
See What Spectre and Meltdown Mean For WebKit
As per Meltdown, Spectre: The password theft bugs at the heart of Intel CPUs
"It affects potentially all out-of-order execution Intel processors since 1995, except Itanium and pre-2013 Atoms."
"It definitely affects out-of-order x86-64 Intel CPUs since 2011."
Affected Intel CPUS are listed at Speculative Execution and Indirect Branch Prediction Side Channel Analysis Method
Also check Intel Security Advisories under Security Advisories
Intel has an analysis of the issue in a PDF at Intel Analysis of Speculative Execution Side Channels
UPDATE: Jan 10 Under Downloads for Processors and then Linux* Processor Microcode Data File there is a new Linux* Processor Microcode Data File dated Jan 8!
On Linux putting this in /etc/firmware and rebooting WOULD apply the file, supported processors include the one for my Intel BOXNUC6i7KYK3 i7-6770HQ NUC Kit - "Intel® Core™ i7-6770HQ Processor (6M Cache, up to 3.50 GHz)"! There is no documentation on that page, will let others try it first!
UPDATE : Jan 12 Intel has reported stability issues after the patches are applied with high end systems rebooting at Intel Security Issue Update: Addressing Reboot Issues "Specifically, these systems are running Intel Broadwell and Haswell CPUs for both client and data center."
UPDATE : 22 Jan as per Meltdown/Spectre week three: World still knee-deep in something nasty Intel later said its more recent Ivy Bridge, Sandy Bridge, Skylake and Kaby Lake architectures are all misbehaving after microcode patching.
UPDATE : 23 Jan as per 'WHAT THE F*CK IS GOING ON?' Linus Torvalds explodes at Intel spinning Spectre fix as a security feature Intel is recommending to STOP deployment of microcode fixes "as they may introduce higher than expected reboots and other unpredictable system behavior"
As per Root Cause of Reboot Issue Identified; Updated Guidance for Customers and Partners Intel said "We ask that our industry partners focus efforts on testing early versions of the updated solution so we can accelerate its release. We expect to share more details on timing later this week."
As per Speculative Execution and Indirect Branch Prediction Side Channel Analysis Method Intel said "For those concerned about system stability while we finalize the updated solutions, we are also working with our OEM partners on the option to utilize a previous version of microcode that does not display these issues, but removes the Variant 2 (Spectre) mitigations. This would be delivered via a BIOS update, and would not impact mitigations for Variant 1 (Spectre) and Variant 3 (Meltdown)."
Intel has a detailed PDF technical note about Spectre protection AS A CPU FEATURE (opt-in by setting IBRS_ALL!) at Speculative Execution Side Channel Mitigations
As per Re: [RFC 09/10] x86/enter: Create macros to restrict/unrestrict Indirect Branch Speculation "Then there's Skylake, and that generation of CPU cores. For complicated reasons they actually end up being vulnerable not just on indirect branches, but also on a 'ret' in some circumstances (such as 16+ CALLs in a deep chain)."
The IBRS solution, ugly though it is, did address that. Retpoline doesn't. There are patches being floated to detect and prevent deep stacks, and deal with some of the other special cases that bite on SKL, but those are icky too. And in fact IBRS performance isn't anywhere near as bad on this generation of CPUs as it is on earlier CPUs *anyway*, which makes it not quite so insane to *contemplate* using it as Intel proposed."
AMD has an advisory at An Update on AMD Processor Security
There are additional known issues for AMD CPUS via the AMD's Platform Security Processor (PSP) see Meltdown, Spectre: The password theft bugs at the heart of Intel CPUs
Firmware and Linux patches will start to appear Jan 9 see Potential Impact on Processors in the POWER family
UPDATE 9th Jan: IBM are holding off on releasing patches as per IBM melts down fixing Meltdown as processes and patches stutter
UPDATE 10th Jan: Potential Impact on Processors in the POWER family
has been updated - POWER7+ and POWER8 patches are available from Fix Centraland "POWER9 patches will be available on January 15."
For IBM Z see The IBM Z Security Portal under Systems integrity
UPDATE 9th Jan: IBM are holding off on releasing patches as per IBM melts down fixing Meltdown as processes and patches stutter
IBM Storage Appliances have been confirmed as not affected see Potential CPU Security Issue "IBM Storage appliances are not impacted by this vulnerability."
Qualcomm is also confirmed as affected see Qualcomm joins Intel, Apple, Arm, AMD in confirming its CPUs suffer hack bugs, too
ARM has an advisory at Vulnerability of Speculative Processors to Cache Timing Side-Channel Mechanism
This advisory mentions "Only affected cores are listed, all other Arm cores are NOT affected."
See the entry for Fujitsu
See the entry for Oracle
See Building a More Secure World with the RISC-V ISA
As per CPU Side-Channel Information Disclosure Vulnerabilities"Cisco will release software updates that address these vulnerabilities"
Dell has 2 Knowledge Base articles, one for Servers,Storage and Networking Microprocessor Side-Channel Vulnerabilities (CVE-2017-5715, CVE-2017-5753, CVE-2017-5754): Impact on Dell EMC products (Dell Enterprise Servers, Storage and Networking)
One for client hardware Microprocessor Side-Channel Vulnerabilities (CVE-2017-5715, CVE-2017-5753, CVE-2017-5754): Impact on Dell products
As per CPU hardware vulnerable to side-channel attacks (CVE-2017-5715, CVE-2017-5753, CVE-2017-5754)"Regarding this vulnerability, we are confirming the impact of our products and how to address it. Release of the first edition is scheduled for January 10, 2018."
Fujitsu SPARC has published a PDF advice at Side-Channel Analysis Method (Spectre & Meltdown) Security Review List of affected Fujitsu Products
This lists affected devices and mentions this "may call for both an operating system update, provided by the OS vendor, and a system ROM update from HPE"
Affected devices are listed on Security Notice Security Notice - Statement on the Media Disclosure of the Security Vulnerabilities in the Intel CPU Architecture Design and Huawei PSIRT will keep updating the SN
There is a Security Advisory at Security Advisory - CPU Vulnerabilities 'Meltdown' and 'Spectre'
As per Reading Privileged Memory with a Side Channel Lenovo "will update this page frequently as fixes are released and new information emerges. Please check back often."
Also "We recommend updating OS and firmware as soon as updates are available."
As per Citrix XenServer Multiple Security Updates "The CPU speculative execution mitigations require system firmware/BIOS upgrades to be applied before becoming fully effective."
For Variant 1 (CVE-2017-5753 'bounds check bypass'), Citrix is not currently aware of any exploit vectors in Citrix XenServer.
Citrix has released hotfixes that contain mitigations for Variant 2 (CVE-2017-5715 'branch target injection') where an attacker running code in a guest VM may be able to read in-memory data from other VMs on the same host. This is independent of the CPU vendor:
| Version | Reference | Link |
|---|---|---|
| Citrix XenServer 7.3 | CTX230790 | Hotfix XS73E001 - For XenServer 7.3 |
| Citrix XenServer 7.2 | CTX230789 | Hotfix XS72E013 - For XenServer 7.2 |
| Citrix XenServer 7.1 LTSR CU1 | CTX230788 | Hotfix XS71ECU1009 - For XenServer 7.1 Cumulative Update 1 |
| Citrix XenServer 7.0 | N/A | Citrix is actively working on a hotfix for this version. The above document will be updated when a hotfix is available. |
Note that these updates are not Livepatchable. Citrix is aware of a potential remaining issue for Variant 2 when using 32-bit PV guests and is actively working on an update for this issue but strongly recommends that customers that have deployed untrusted 32-bit PV guests consider transitioning to HVM-based guests.
Customers using End of Maintenance versions of Citrix XenServer, i.e. Citrix XenServer version 6.0.2 Common Criteria, 6.2 SP1 and 6.5 SP1 are strongly recommended to upgrade to a more recent version.
Citrix is actively working on additional mitigations for Variant 3 (CVE-2017-5754 ' rogue data cache load') where an attacker running code in a 64 bit PV guest VM running on an Intel CPU may be able to read in-memory data from other VMs on the same host, but strongly recommends that customers that have deployed untrusted 64-bit PV guests on Intel CPUs consider transitioning to HVM-based guests.
Nutanix has a PDF advisory for their products at Side-Channel Speculative Execution Vulnerabilities January 2018
"Please check the Nutanix Support Portal for the latest update.
NVIDIA have a security update at Security Bulletin: NVIDIA Driver Security Updates for CPU Speculative Side Channel Vulnerabilities
UPDATE: 15th Jan Oracle still silent on Meltdown, but lists patches for x86 servers among 233 new fixes in the comments section
"Two quotes from an Oracle Support ticket, reported by a customer on this forum post."
Is SPARC architecture affected by Spectre / Meltdown vulnerabilities?
"Oracle is aware of the recently disclosed security vulnerabilities. Oracle is investigating the impact on the Oracle product line and will produce patches for any affected Oracle product. Patches for affected Oracle products will be announced on the Critical Patch Update page at Critical Patch Updates, Security Alerts and Bulletins
"Oracle will not provide any additional information other than the patches announced in the mentioned CPU alerts. We will not provide advanced notification or additional details about the security vulnerability."
"Please check the CPU page including the Third Party Bulletin for updates. Solaris fixes (where applicable) will also be listed in the MOS MOS note 1448883.
UPDATE: Jan 16 As per Oracle says SPARCv9 has Spectre CPU bug, patches coming soon
"Oracle has told users of its SPARC-powered platforms that they have the Spectre processor design flaw."
“Oracle believes that certain versions of Oracle Solaris on SPARCv9 are affected by the Spectre vulnerabilities.”
"Oracle is working on producing the patches for all affected versions that are under Premier Support or Extended Support.”
"The note also clears Solaris on SPARCv9 of the Meltdown design cockup."
NOTE: Solaris already runs kernal and userland in seperate address spaces
“Oracle OS and Oracle VM patches for CVE-2017-5715 will include updated Intel microcode”
As per Biggest vuln bombshell in forever and storage industry still umms and errs over patches Nexenta's VP for marketing and channels, Don Lopes, said:
"Contrary to compute platforms or hyperconverged solutions, our products are delivered as closed software appliances and do not allow running third-party software to run on them."
"Due to this, they aren't exposed to exploits. In the cases where our software is run as a VM or a Docker container, we do recommend that customers patch the underlying OS and hypervisors."
"We provided these details and have spoken to a number of our customers and partners who have accepted and are happy with our communication."
As per Biggest vuln bombshell in forever and storage industry still umms and errs over patches Object storage supplier Scality's chief product officer Paul Speciale said:
"the Scality RING software is in nearly all cases deployed in our customers' secure data centres. This means our software is behind the multiple layers of firewalls and security devices, and accessed only by customer applications versus direct access on the internet. This insulation means we are much less susceptible to outside malicious access."
"While we do deploy on standard x86-based servers, we don't present a general-purpose server to the outside world. For example, the RING restricts access to only the necessary network ports needed for operations. We also have our own software stack virtualizing the underlying hardware, and our own management software stack."
As per Biggest vuln bombshell in forever and storage industry still umms and errs over patches A spokesperson told us:
"only a small subset of customers are running third-party code within Purity Run, which we released last year."
""We know who all of these customers are and have already contacted each of them personally. We would expect no impact on non-Purity Run storage performance and minimal impact on Purity Run performance for Spectre mitigations."
"We'll be working to help users assess Meltdown mitigations for any guest environments or apps they are running within Purity Run, though the same updates would be necessary regardless of whether they are running on a virtualized platform or bare metal."
As per Now Meltdown patches are making industrial control systems lurch:
SCADA vendor Wonderware admitted that Windows Server 2012 patch January 4, 2018—KB4056896 (Monthly Rollup) causes instability for Wonderware Historian and the inability to access DA/OI Servers through the SMC
This is covered in advistory Important! Tech Alert 287
Rockwell Automation revealed that Windows Server 2012 patch January 4, 2018—KB4056896 (Monthly Rollup) caused issues with Studio 5000, FactoryTalk View SE, and RSLinx Classic (a widely used product in the manufacturing sector)
See Synology-SA-18:01 Meltdown and Spectre Attacks
See K91229003: Side-channel processor vulnerabilities CVE-2017-5715, CVE-2017-5753, and CVE-2017-5754
See Announcement regarding XSA-254 (Meltdown and Spectre attacks)
See PSIRT Advisory CPU hardware vulnerable to Meltdown and Spectre attacks
See Processor Speculated Execution Vulnerabilities in NetApp Products
See Why Raspberry Pi isn’t vulnerable to Spectre or Meltdown
"The lack of speculation in the ARM1176, Cortex-A7, and Cortex-A53 cores used in Raspberry Pi render us immune to attacks of the sort."
The following were also used to collect the information provided in this document:
| Source | Reference |
|---|---|
| Sqlskills Glen Berry | Microsoft SQL Server Updates for Meltdown and Spectre Exploits |
| SQLHA Alan Hirt | The No Good, Terrible Processor Flaw and SQL Server Deployments – Nearly Everything You Need To Know |
| Lenovo - many references under "Advisories and Patch Guidance: | Reading Privileged Memory with a Side Channel |
| Meltdown and Spectre | Meltdown and Spectre |
| A collection of Meltdown/Spectre postings | 1.2 solaceattack - Skyfall and Solace
As per Skyfall and SolaceSkyfall and Solace are two speculative attacks based on the work highlighted by Meltdown and Spectre. "Full details are still under embargo and will be published soon when chip manufacturers and Operating System vendors have prepared patches." 1. Jan2017 Issues |